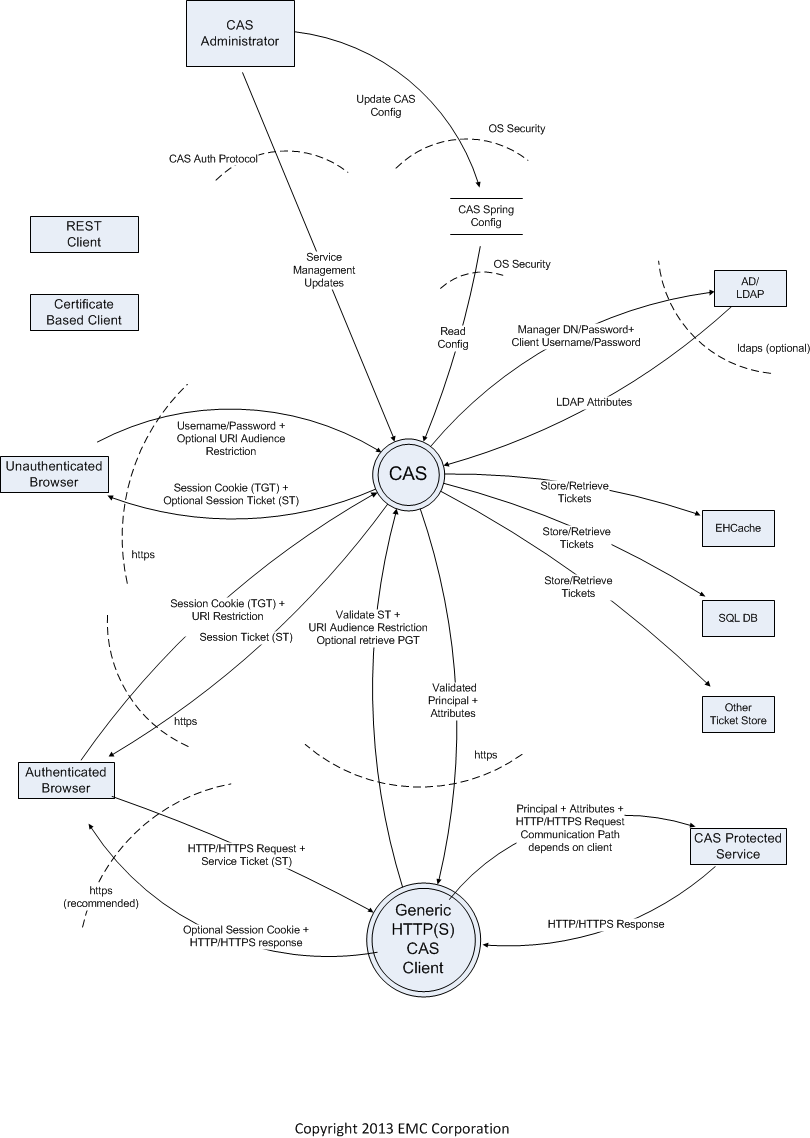
"Threat modeling is an approach for analyzing the security of an application" (see https://www.owasp.org/index.php/Application_Threat_Modeling). One step in the threat modeling is the creation of a dataflow diagram (DFD) of the system so that all attack surfaces can be identified. The following diagram is a first draft of the DFD
- Visio Source File: CAS DFD.vsd
- Visio File in VDX format: CAS DFD.vdx